¶ VPN
Most intranet services are brokered through auth.k-space.ee — VPN is rarely needed.
VPN provides access to VLAN 23 "management", which is reserved for IPMI (iLO, IDRAC), SNMP, etc. It is meant for users hosting physical servers.
To receive a configuration file, ask and provide a reason to a Network admin.
VPNs today are MikroTik native WireGuard, issued manually.
¶ Using WireGuard config
The received config is accepted by various tooling, including in MacOS and Windows.
Basic configuration on Linux:
- Move/paste contents to
/etc/wireguard/k-space.conf - Connect:
systemctl start wg-quick@k-space
¶ History
- An OpenVPN container (docs) deployed on router2.k-space.ee TCP 443 / UDP 1194. Credentials manually generated. Superseeded by native wg.
- Certidude with AD self-service browser-generated configs. Abandoned for its complexity.
¶ Known issues
From OpenVPN era.
¶ VPN connected, but can't access K-SPACE addresses
Tailscale and a few other always-on VPNs conflict with the CGNAT IPv4 subnet (100.64.0.0/10), which is currently used in K-SPACE. Turn off Tailscale, and reconnect (every time) / ask to redo the network.
¶ *.k-space.ee not accessible.
The VPN is meant for remote access to the local networks. Don't route porn through the VPN.
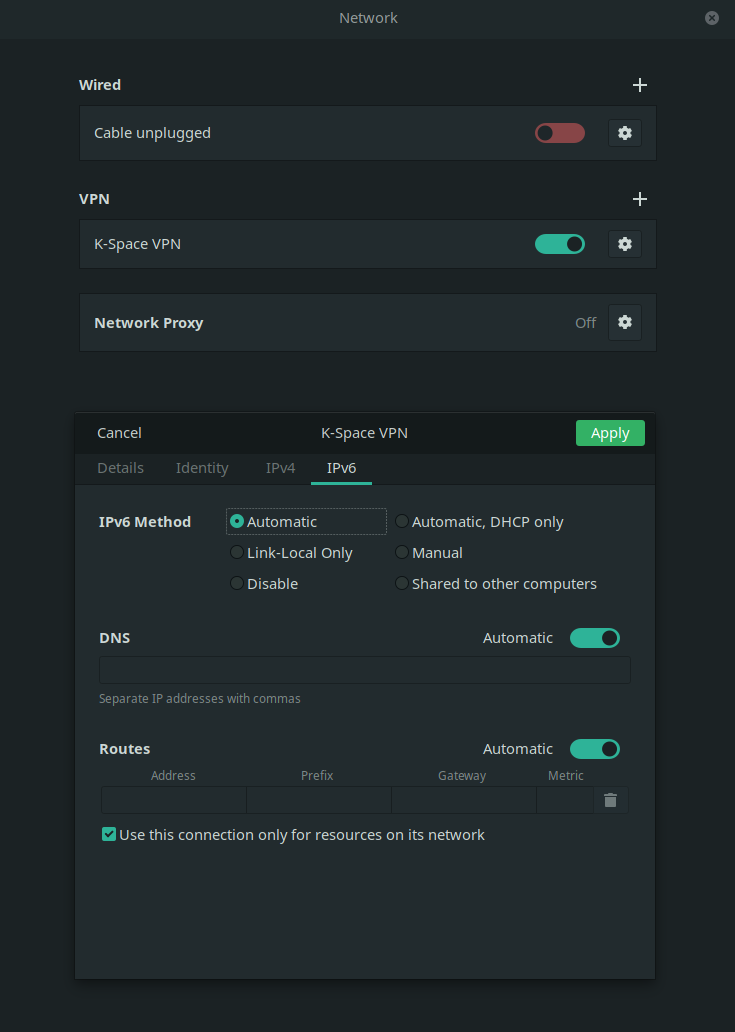
¶ Gnome GUI:
Check Use this connection only for resources on its network for both IPv4 and IPv6.
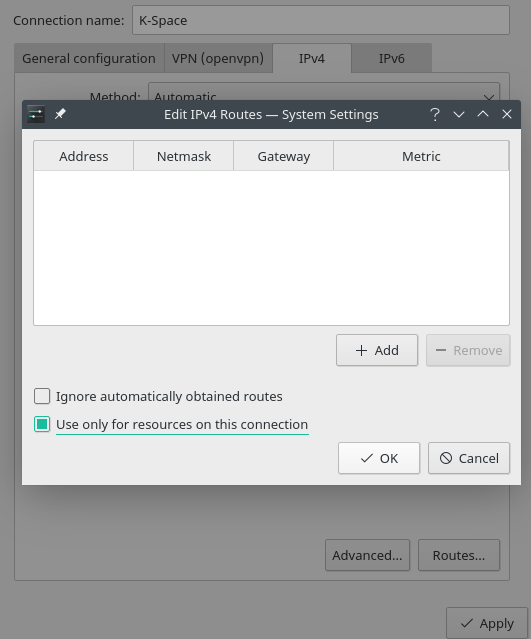
¶ NetworkManager (Plasma, i3, …) GUI:
Check 'Use only for resources on this connection' for boht IPv4 and IPv6. Access the dialogue via the 'Routes…' button. Don't forget to apply changes.
¶ Docker default address pool
172.16.0.0/12 subnet is used in the K-SPACE internal network.
When using VPN these subnets are pushed to your local machine. This will clash with local Docker bridge which uses a same subnet.
Edit /etc/docker/daemon.json and change default address pool:
{
"default-address-pool":
[
{"base":"10.32.0.0/16","size":60000}
]
}